Data Security in the Digital Age
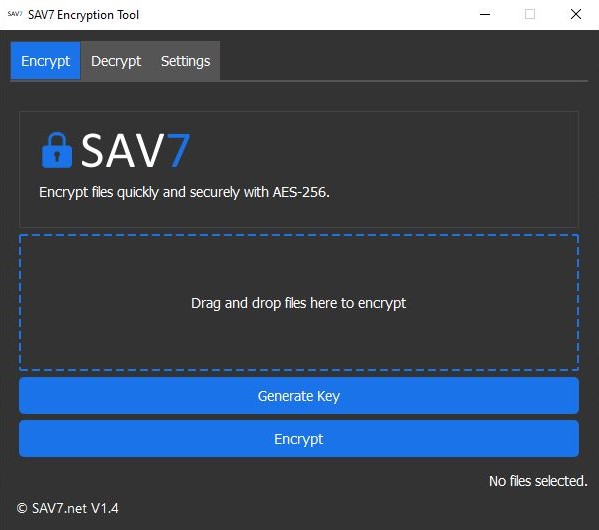
In the digital age, data security is a central concern for both individuals and organizations alike. The increase in cyber threats necessitates robust measures to protect sensitive information from unauthorized access. SAV7 is an advanced encryption tool that provides a secure, user-friendly solution for data encryption and decryption.
Main Features
AES-256 Encryption
AES-256 (Advanced Encryption Standard with a 256-bit key) is globally recognized for its high level of security. This encryption method is used by governments, financial institutions, and security-conscious organizations to protect sensitive information.
- Strong Security: AES-256 is resistant to all known practical attacks, ensuring that your data remains secure.
- High Performance: Despite its strong security, AES-256 is optimized for high performance, allowing fast encryption and decryption processes.
Key Expiration Management
SAV7 allows users to set expiration dates for their encryption keys. This feature enhances security by ensuring that encrypted data is only accessible within a specified time frame.
- Time-Limited Access: Set an expiration date for your encryption keys, after which the keys will become invalid.
- NTP Synchronization: The application synchronizes with Network Time Protocol (NTP) servers to ensure accurate timekeeping for key expiration.
Secure File Deletion
In addition to encryption, SAV7 offers secure deletion features to ensure that sensitive data is permanently removed from your storage devices.
- Multiple Overwrites: Files are overwritten multiple times with random data, making recovery virtually impossible.
- Regulatory Compliance: Meets standards for secure deletion and ensures compliance with data protection regulations.
Everything You Need to Know About Encryption Software
In an increasingly digital world, protecting sensitive data is more important than ever. Encryption software plays a crucial role in safeguarding your information from unauthorized access. But what exactly is encryption software, and why is it so important?
What is Encryption Software?
Encryption software is a program that transforms data into an unreadable format, which can only be decrypted with a specific key. This ensures that only authorized individuals have access to the information. Whether it’s personal data, business documents, or financial information – encryption protects your data from cybercriminals.
Why is Encryption Software Important?
The importance of encryption software cannot be overstated. In an era where data breaches and hacking attacks are becoming more common, encryption adds an extra layer of security. It protects not only against external threats but also against internal security risks.
Types of Encryption Software
There are various types of encryption software, each suitable for different applications and security requirements:
- File Encryption: Protects individual files or folders on your computer or in the cloud.
- Disk Encryption: Encrypts the entire hard drive of your device to secure all stored data.
- Email Encryption: Ensures your email communication remains private and can only be read by the intended recipient.
- VPNs (Virtual Private Networks): Protect your internet connection and hide your online activities from prying eyes.
How to Choose the Right Encryption Software
When selecting the right encryption software, consider the following factors:
- Security Level: Ensure the software uses strong encryption algorithms like AES (Advanced Encryption Standard).
- User-Friendliness: The software should be easy to install and use, even for those without technical expertise.
- Compatibility: Make sure the software is compatible with your devices and operating systems.
- Cost: Check if the cost of the software is justified by the security features it offers.